
VOICE Home Page: http://www.os2voice.org
Newsletter Index
< Previous Page | Next Page >
Feature Index

VOICE Home Page: http://www.os2voice.org |
May 2004
Newsletter Index
|
| By Robert Henschel © May 2004 |
There are a lot of ways to protect personal information under OS/2. For example,
some programs offer the possibility to password-protect files. Lotus Word Pro and OpenOffice.org
are among them. When saving a document, one has to enter a password and now this file can only
be opened by entering the same password. (Of course, there is always the possibility to use crack
programs to gain access to password-protected files. Such tools may not be available for OS/2, but
that does not stop people from using them against OS/2 documents!)
If valuable information is not stored in simple documents, one can always use "ZIP" to
protect any kind of data. All files are stored in a ZIP-Archive and this archive can be protected
with a password. Under OS/2, one can use PKZIP. (ZIP-Archives are especially vulnerable against
password cracking programs. There are ready-to-use cracking tools available in the Internet!)
Both procedures do have some disadvantages. On one hand one has to trust the companies
that create office productivity applications. There is always the possibility that the encryption
is not implemented correctly or that it can be circumvented in some way. On the other hand one has
to extract the data from an archive into a temporary directory and after using it one has to
recreate the archive. (And the temporary copies of the files need to be deleted!)
A more elegant solution to those problems is an encrypting file system. AEFS is just one of the
available solutions; the Cipher Plug-In for NetDrive is another. Encrypting file systems encrypt
all data that is stored on a particular drive without interaction by the user. They do not depend
on the applications that are used to manipulate the data.
AEFS is an installable file system for OS/2 and eComStation. It can be used just like HPFS or
JFS except that partitions do not need to be formatted. AEFS-drives can be used by any program
that can access files. To make this possible, AEFS simply creates a new drive letter. All files
that are stored on this new drive are automatically encrypted. There is no user-interaction
required.
To avoid having to partition the hard drive for this new drive, AEFS maps the new drive
letter to an existing directory. It does not matter what file system is used on this drive. This will
be explained in more details later.
Encryption is performed using well known algorithms like Rijndael and Twofish. The current version
of AEFS limits the length of the key to 256 bit. It has to be said that 256 bit is still
considered safe by current standards, but that could change rather fast in the future.
AEFS is available for OS/2 and Unix-like operating systems. Because of this, the EMX runtime
is required (version 0.9d Fix 4).
The archive contains the source code of AEFS as well as a binary version. If the source code
is not of interest to you, only the directory \bin and the files readme.txt
or readme.inf are needed. After extracting the files to the final directory
two lines have to be added to CONFIG.SYS.
IFS=[bin-directory]\stubfsd.ifs AEFS
RUN=[bin-directory]\aefsdmn.exe
[bin-directory] is the \bin subdirectory of the installation
directory of AEFS.
To make working with the AEFS utilities easier, it is a good idea to add the
[bin-directory] to the PATH of CONFIG.SYS. This
is not necessary, but makes it easier. A reboot is required to activate the changes.
To work with AEFS it is necessary to have an empty directory that takes the encrypted data,
for example D:\Crypto. The directory can be located on any drive, no matter what
the file system is. It can also be a network drive. If you want to use the mkaefs
utility without a second command line parameter, the directory must not exist. The second thing that is needed is a new drive letter, for example "x".
Now one can create the AEFS file system. To do that, enter the following:
mkaefs d:\crypto
To create the AEFS file system, it is necessary to enter the password now.
To use the new AEFS file system, it has to be assigned to a drive letter. This can be done with the following command:
mntaefs.exe x: d:\crypto
When assigning the AEFS file system to a drive letter, the password is needed. One can only open the file system if the password is correct. After entering the correct password all programs can access the new drive "x".
Releasing the file system can be done with the following command:
umntaefs.exe x:
After releasing the file system, the data that was stored on drive "x"
can only be accessed through the encrypted files stored in D:\Crypto.
It is a good idea to back up personal data. This is also true for encrypted personal data!
Backing up the data is as easy as burning a copy of the encrypted directory D:\Crypto
to a CD or packing everything in this directory in to a ZIP archive. Of course, it is also
possible to back up the original not encrypted data directly from drive "x".
Mozilla creates a profile for every user. Among other things, this profile holds the bookmark file and history. Placing this profile on an AEFS drive is quite easy. First of all, one has to start the profile manager of Mozilla and create a new profile.
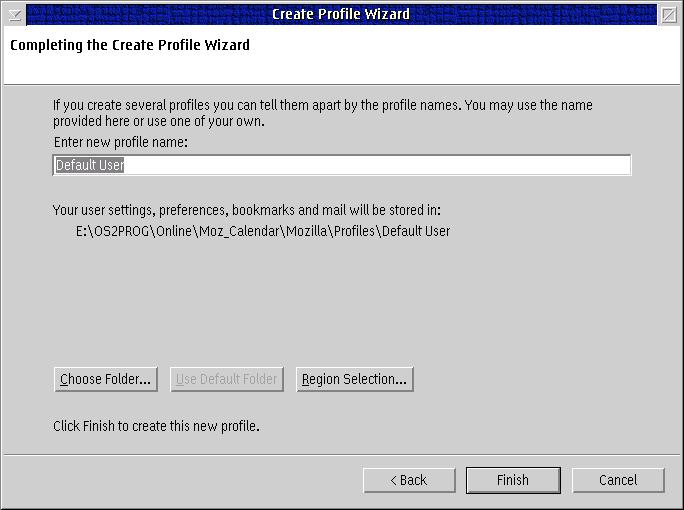
Fig.1: Creating a new profile
The path for the new profile should be changed so that it points to the root of drive "x".
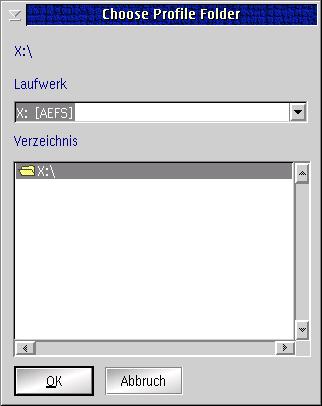
Fig.2: Changing the path for the profile
(Drive "x" is an AEFS file system. It has been created using the AEFS utilities.)
The Mozilla profile must only be accessible while Mozilla is running. To increase security,
it will be opened just before Mozilla is started and released right after Mozilla is closed. One can
do this manually every time, but using a CMD file is more convenient.
@echo off
mntaefs.exe x: d:\crypto
IF ERRORLEVEL 1 goto FAILED
Mozilla.exe
umntaefs.exe x:
GOTO END
:FAILED
@echo Wrong Password ?!
PAUSE
:END
This CMD file should be saved into the Mozilla directory, the same directory where mozilla.exe
resides. (A shadow of the file can be placed on the desktop.)
Starting the CMD file will ask the user for the password for the AEFS file system.
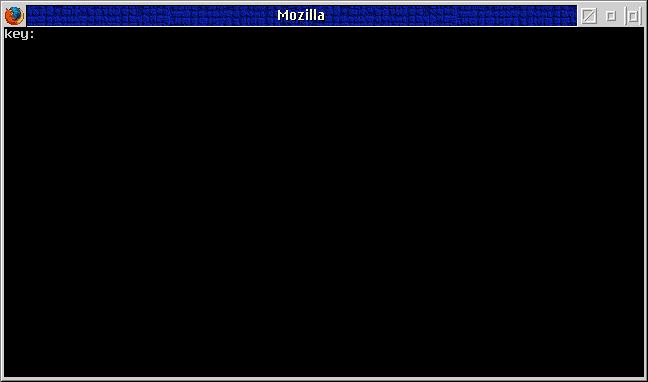
Fig.3: Enter password
Entering the correct password will start Mozilla. If the wrong password is entered, a short message is displayed and after hitting a key the window will be closed.
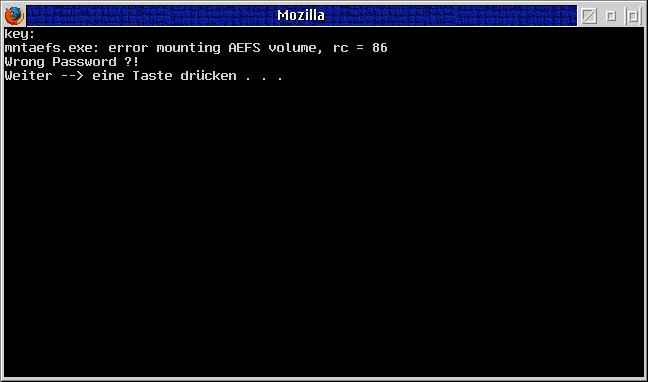
Fig.4: Wrong password
After Mozilla is closed, the AEFS file system is released and the profile directory is no
longer accessible via drive "x".
The profile directory is on drive "x" and contains the personal settings
for Mozilla.
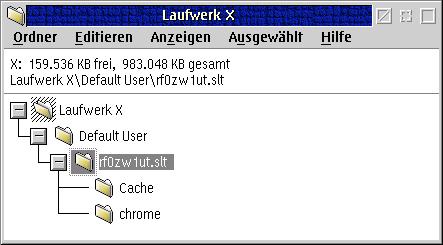
Fig.5: Mozilla profile - not encrypted
The real data is stored in the directory d:\crypto and is encrypted.
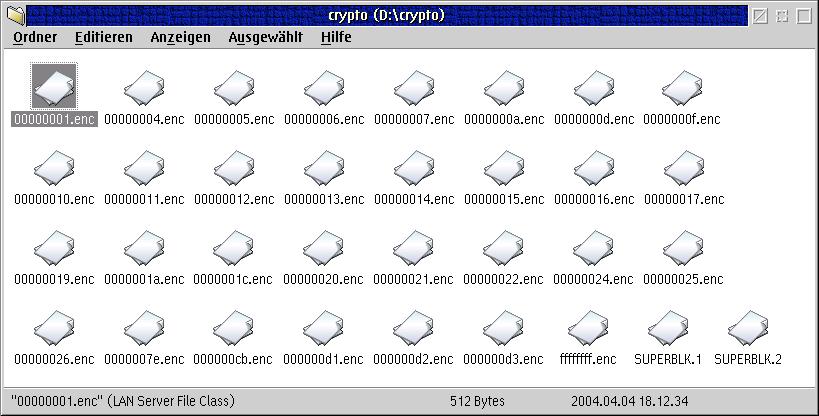
Fig.6: Mozilla profile - encrypted
All utilities accept --help as a command line argument. So it is possible to
get detailed help for all utilities on the command line. Even more information is available in
the ReadME of AEFS.
Creates a new, empty AEFS file system. One needs to specify the path where the encrypted
files will be stored. One can also specify the encryption algorithm, but this is optional.
Example: mkaefs d:\crypto
Checks an AEFS file system and corrects errors if possible. (This can be compared to
chkdsk for HPFS or JFS) It is a good idea to create a backup of the encrypted data
before using this utility!
Example: aefsck d:\crypto
Assigns a drive letter to an AEFS file system. It is also possible to mount the file system
read only!
Example: mntaefs x: d:\crypto
Releases an AEFS file system.
Example: umntaefs x:
Decrypts a specific file of an AEFS file system.
This utility should only be used by experienced users!
aefsdmn is started in CONFIG.SYS and its parameters are discussed in more detail in the ReadME. aefsparm can be used to change the parameters of aefsdmn while it is running.
It is not possible to create an AEFS file system within an AEFS file system.
The length of the key that is used for encryption is limited to 256 bit.
All AEFS file systems should be released before an OS/2 shutdown is performed. There is a problem with data that could still be in the AEFS cache and cannot be written to the underlying file system at the time that AEFS detects the shutdown. More information is available in the AEFS ReadME. It is a good idea to use one of the available shutdown utilities to release all AEFS file systems shortly before a shutdown is performed.
Files within an AEFS file system are encrypted on a per file basis. Thus it is possible to find out about the file sizes of the real files stored on the AEFS file system.
When files are changed in the AEFS file system, the time stamp of the encrypted file is changed as well. Thus it is possible to gain some information about the files by looking at the time stamp of the files. (The same is also true for sectors within the encrypted files.)
Parts of unencrypted data could be swapped to disc (SWAPPER.DAT). Because AEFS utilities are normal OS/2 programs, it is possible that parts of the AEFS memory get swapped to disc if low memory is detected.
Programs that save data to an AEFS file system could also save data to the TEMP directory. Those temporary copies do not get deleted when the AEFS file system is released!
Using AEFS file system with the WPS creates handles in the OS2.INI file!
The ReadME of AEFS lists all required programs and files for compiling AEFS. Useful MAKEFILEs are provided as well. AEFS does compile with the latest GCC of InnoTek as well as older GCC compilers. Among other things, one needs:
Microsoft C 6.00 (freely available via OS/2 DDK)
FSD Helper Library (freely available)
GCC (GNU, and as such of course free)
to compile the NFS part of AEFS, you need "rpcgen"
"rpcgen" can be taken from FreeBSD and compiled on OS/2 without much trouble
All MAKEFILEs are based on the Unix standard. To use them instead of creating new MAKEFILEs one needs a full Unix environment on OS/2. (SH, BINUTILS, GNUUTILS, GNUMAKE, AUTOCONF, etc.)
References:
|
Feature Index
editor@os2voice.org
< Previous Page | Newsletter Index | Next Page >
VOICE Home Page: http://www.os2voice.org